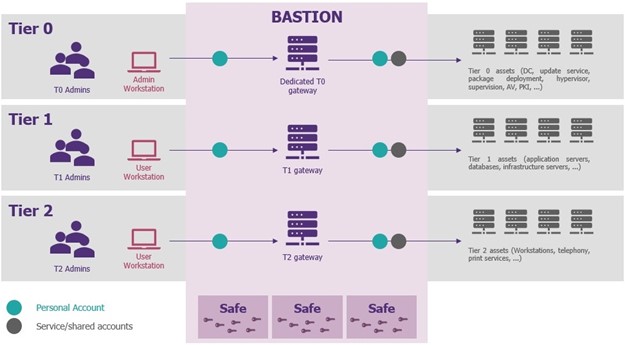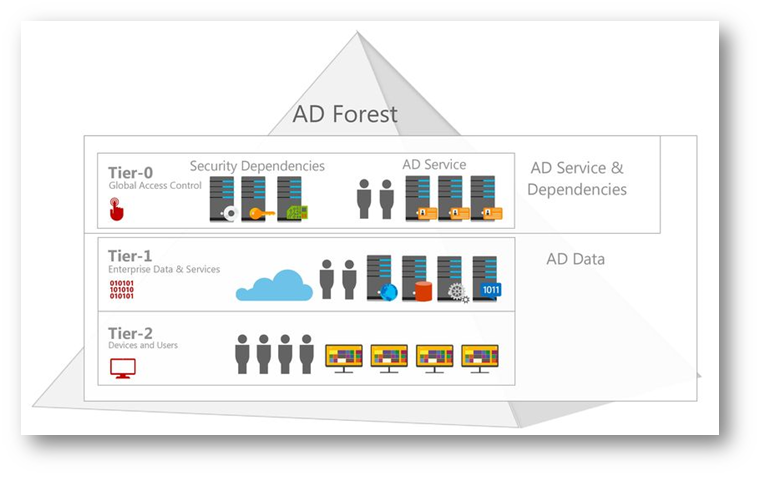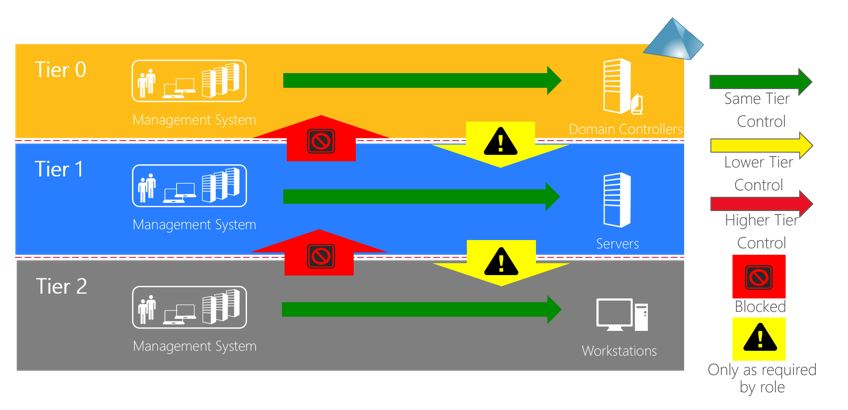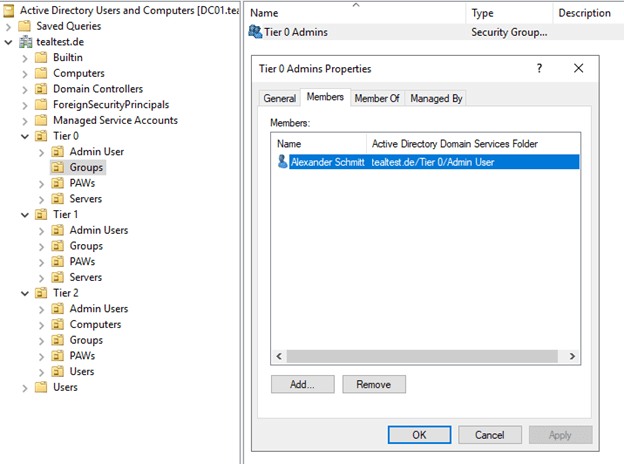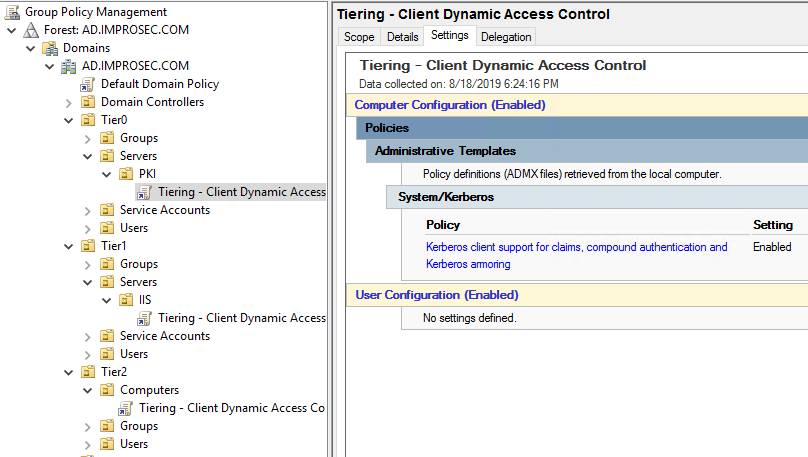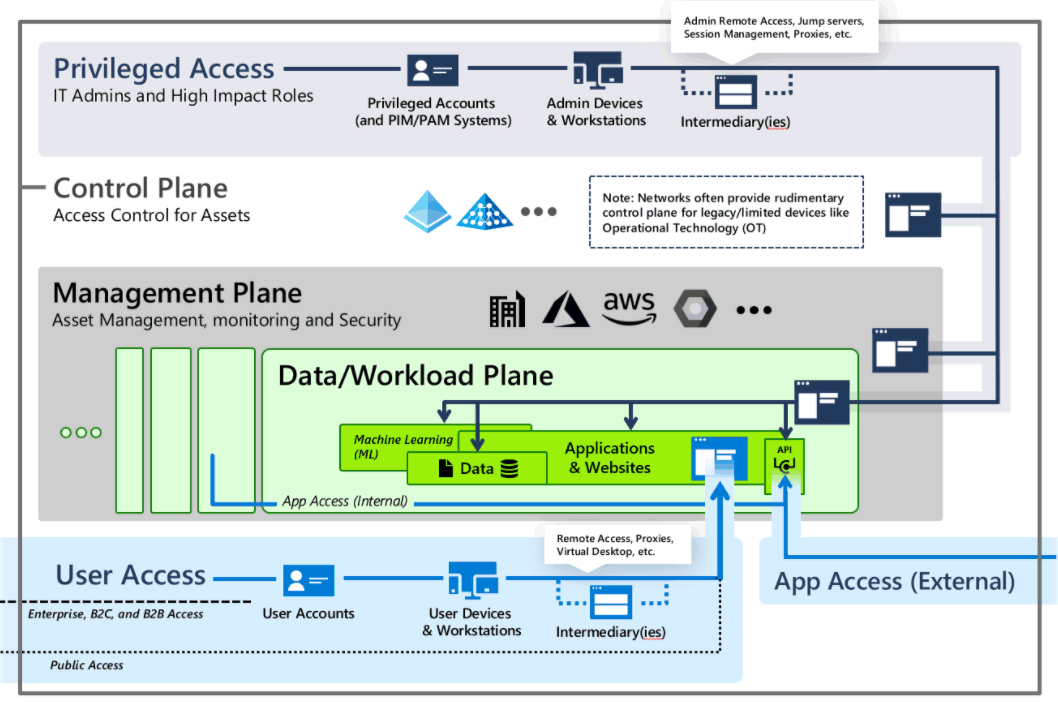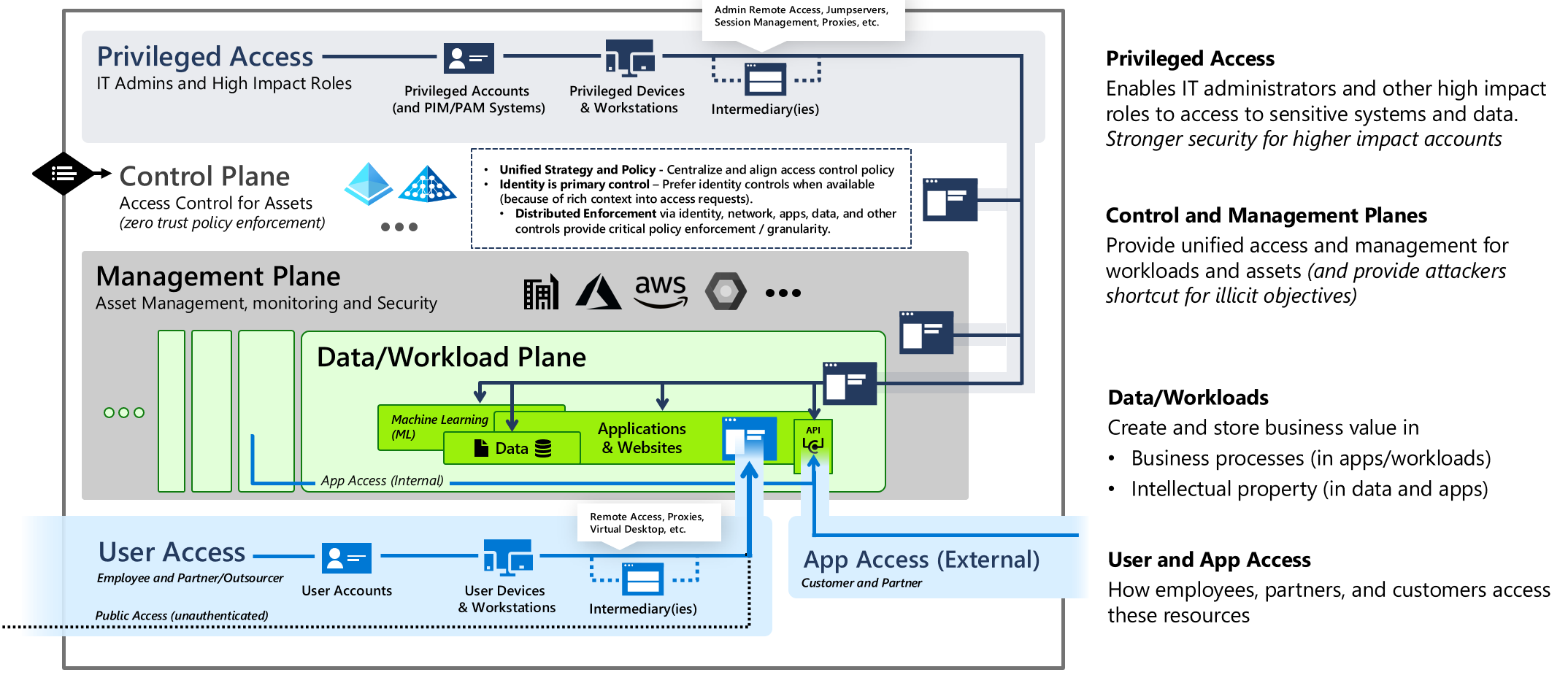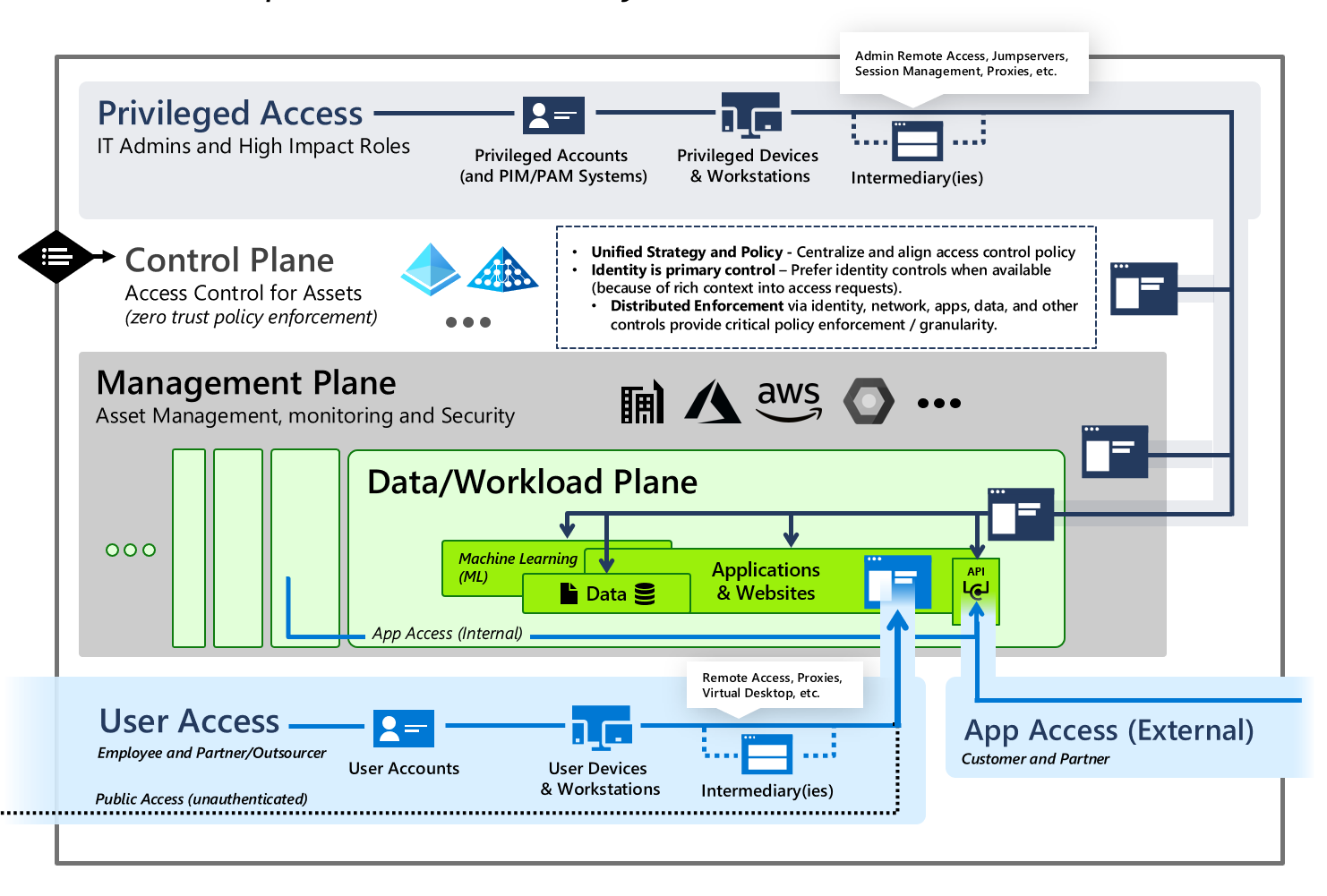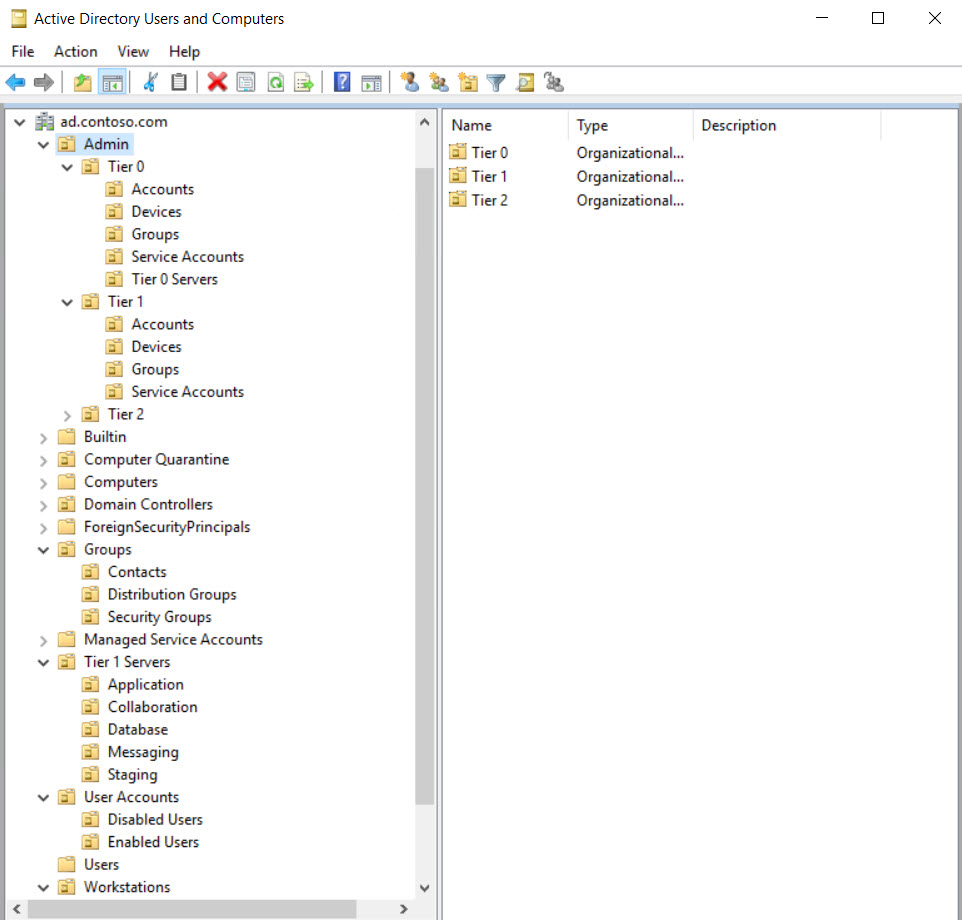
Set Up Active Directory to Support Tiered Administration and Privileged Access Workstations - Petri IT Knowledgebase
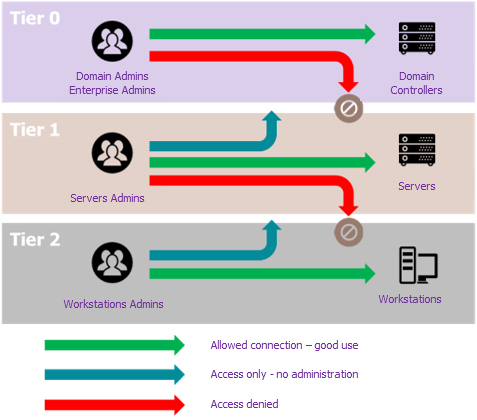
Security bastion (PAM) and Active Directory tiering mode: how to reconcile the two paradigms? - RiskInsight

Download Designing Privileged Access Workstations (PAWs) in an Active Directory Tier-0 Environment Whitepaper | DemandTalk
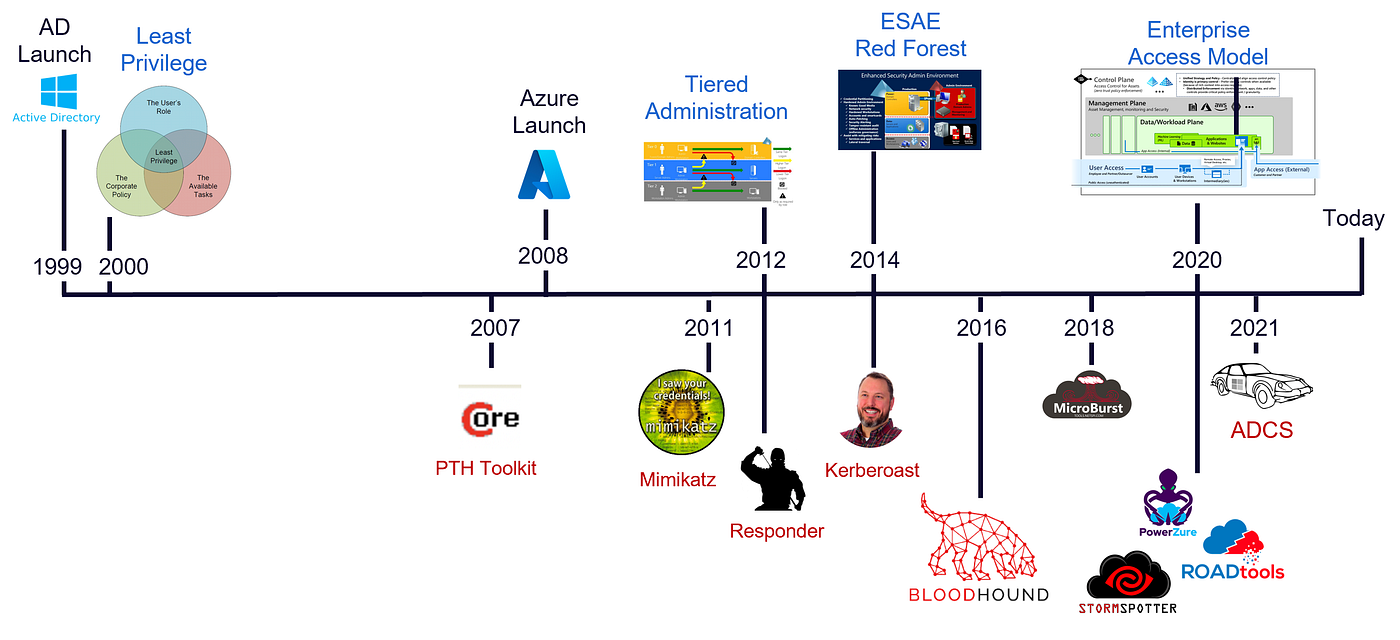
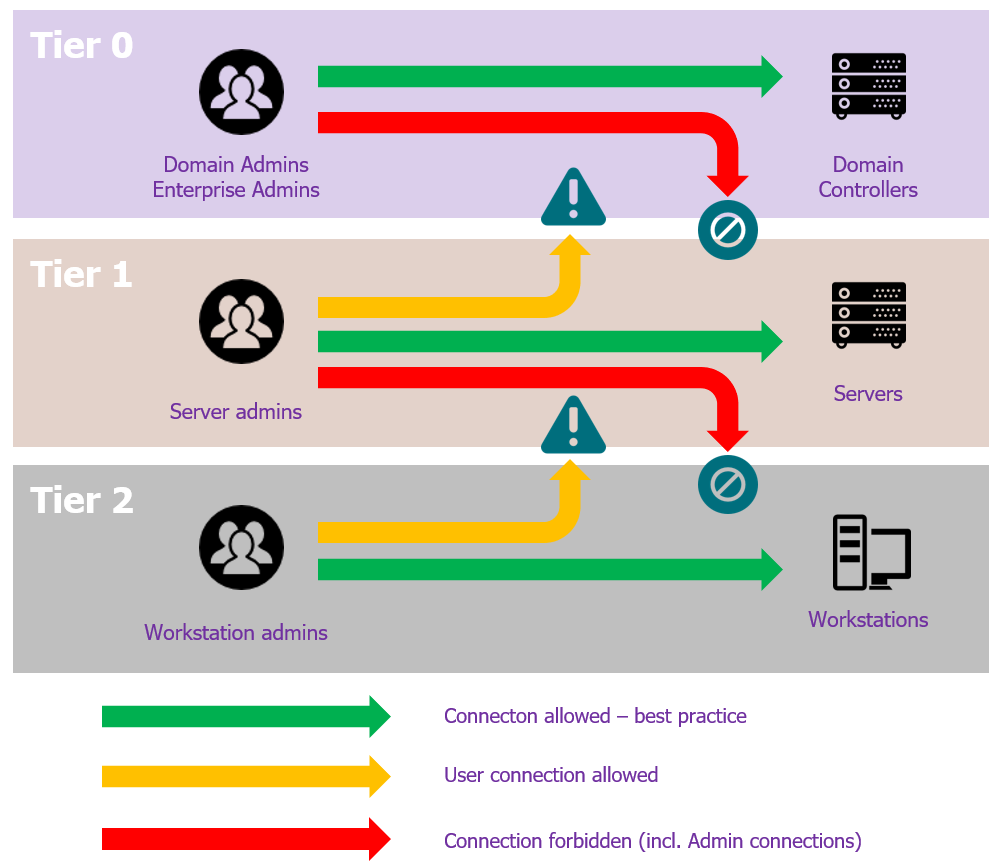
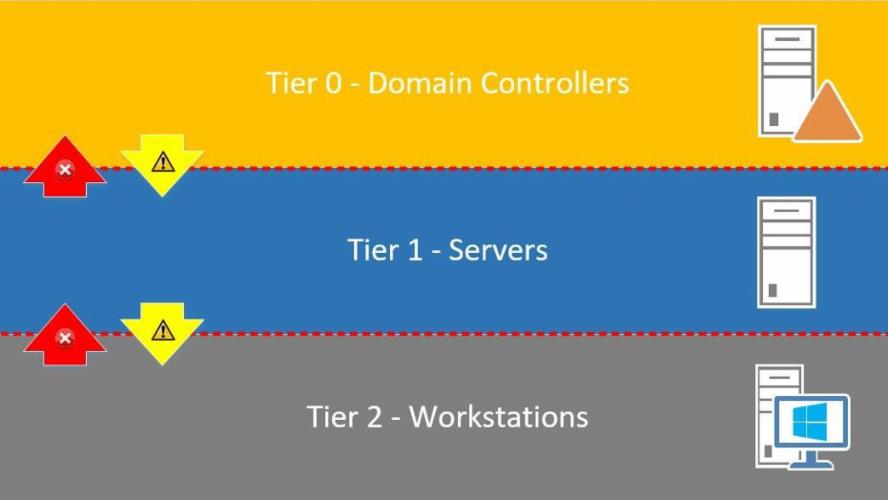
What is Tier Zero — Part 1. Tier Zero is a crucial group of assets… | by Jonas Bülow Knudsen | Posts By SpecterOps Team Members
![转帖]Mitigate Credential theft with Administrative Tier Model-International vision-看雪-安全社区|安全招聘|kanxue.com 转帖]Mitigate Credential theft with Administrative Tier Model-International vision-看雪-安全社区|安全招聘|kanxue.com](https://bbs.kanxue.com/upload/attach/202003/833800_N4DWJMN89REA3TK.jpg)
转帖]Mitigate Credential theft with Administrative Tier Model-International vision-看雪-安全社区|安全招聘|kanxue.com
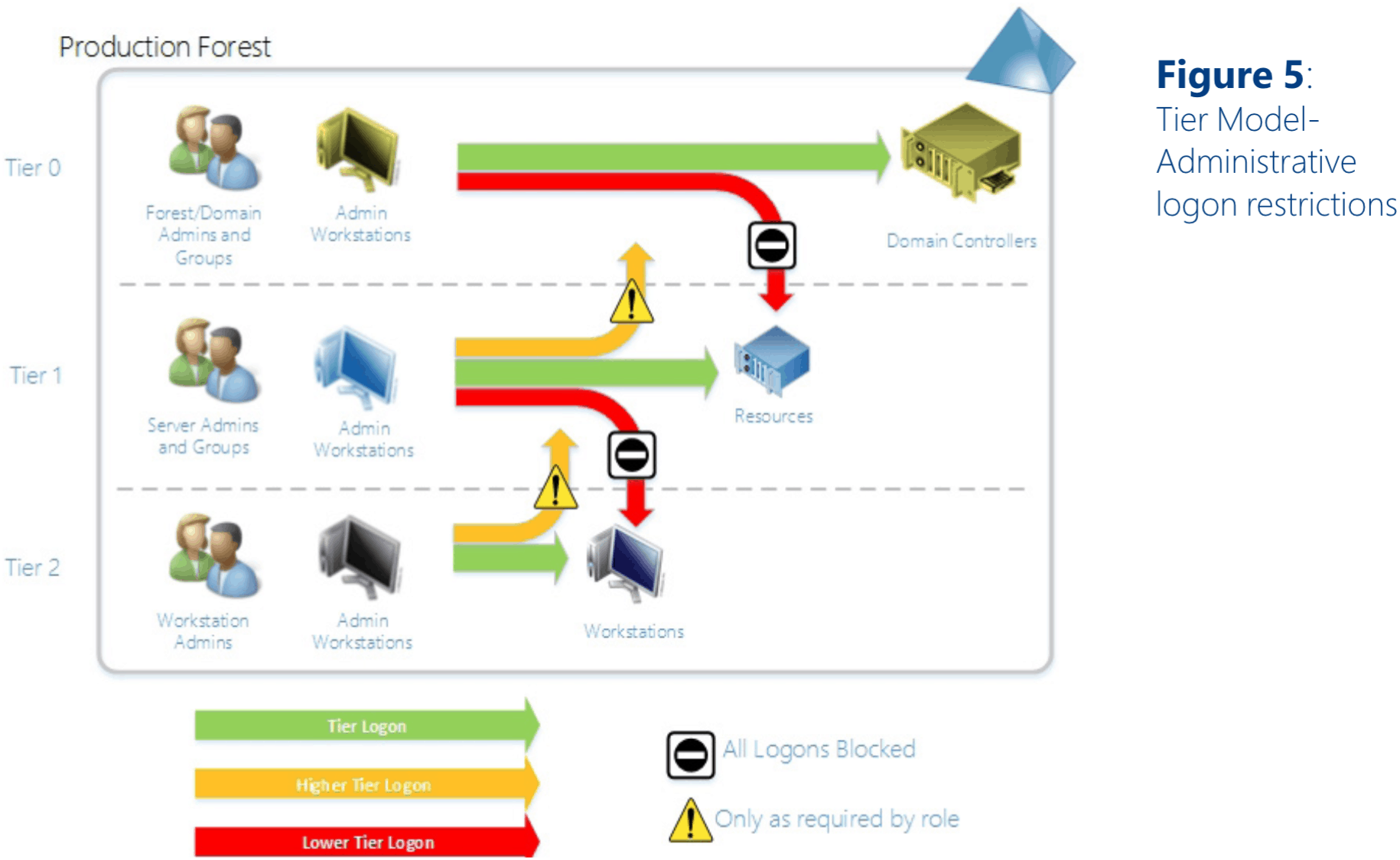
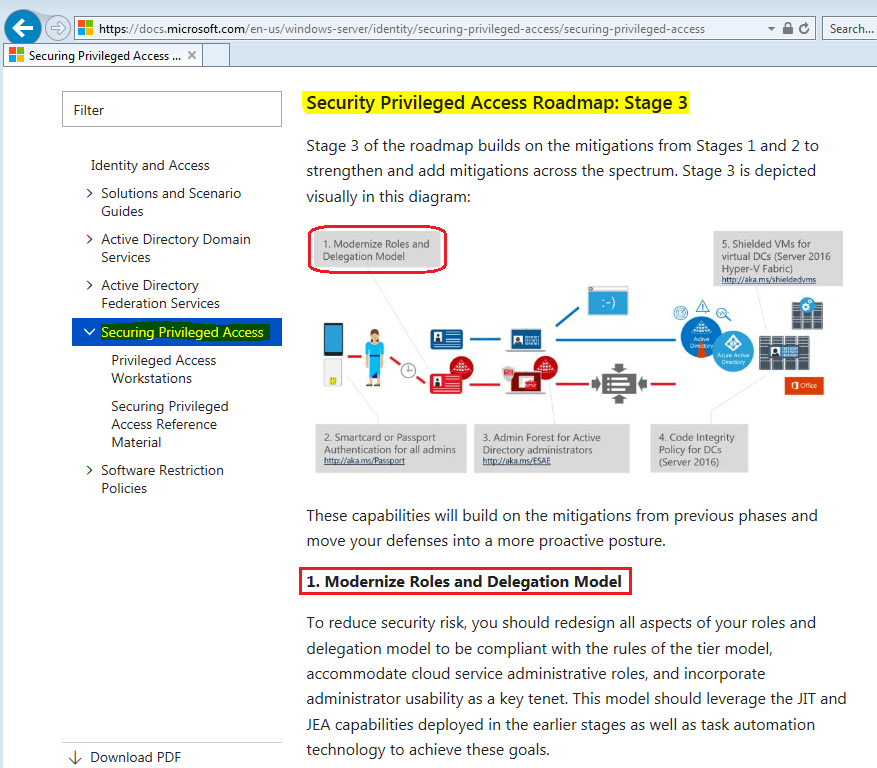
Good Riddance, Red Forest: Understanding Microsoft's New Privileged Access Management Strategy - Semperis

What is Tier Zero — Part 1. Tier Zero is a crucial group of assets… | by Jonas Bülow Knudsen | Posts By SpecterOps Team Members